BPM Was Never Designed Around the Person Doing the Work. That's the Whole Problem.
A conversation with Cristian Salanti, Digital Workplace Strategist Here's an uncomfortable truth about...
In just two years since the BYOD trend has taken off, the response from business and IT has shifted dramatically. In early 2012, most organizations were wary if not downright resistant to the idea of...
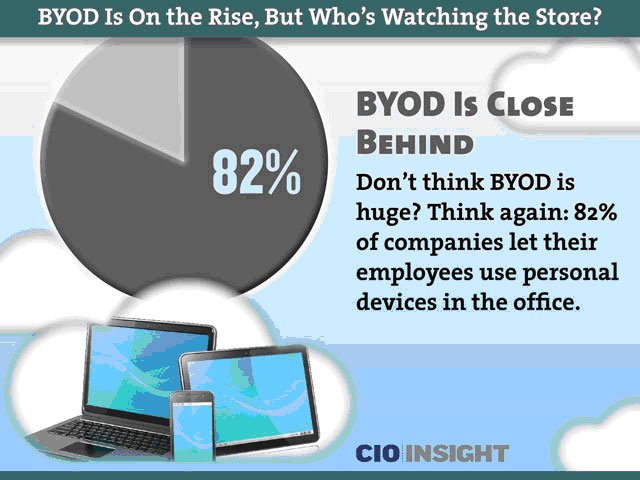
In just two years since the BYOD trend has taken off, the response from business and IT has shifted dramatically. In early 2012, most organizations were wary if not downright resistant to the idea of employee-owned devices in the workplace, viewing them as an annoyance at best and a major security risk at worst.
Now, a mere 24 months later, not only do 82% of companies permit the use of personal devices at the office, but “many firms around the world are mandating that employees bring their own products into the office to accomplish their work” according to CIO Insight.
In parallel with the embrace of BYOD, enterprises are also sanctioning much greater use of cloud-based services and applications. Per the recent survey of IT leaders cited by CIO Insight:
The appeal of BYOD to companies is obvious: saving money. With BYOD, a business has no hardware costs; generally lower airtime costs (because these are often split with users); lower training costs (users know their own devices); and support costs generally no higher than before BYOD (thanks to improved cross-device support tools). It can also increase worker productivity.
But despite the significant progress that’s been made in addressing the causes of early business and IT apprehension, considerable security concerns remain. According to this study:
Yikes! So what can companies do?
While security vulnerabilities are nearly impossible to eradicate completely, there are a number of steps companies can take today to reduce their exposure. These half-dozen recommendations are a start:
Despite the security risks posed by cloud computing and BYOD, there’s no turning back. The convenience, cost savings and productivity gains are too significant for enterprises to reverse course now, even if employees acquiesced to that (which except in rare cases, they won’t). Instead, employers need to keep abreast of new technologies and practices which will enable them to realize the benefits of BYOD and cloud computing, while progressively reducing associated security threats and compliance risks.
For more information:
– See how Kinetic Data products can help with BYOD management, security and compliance.
– Download the white paper, Enterprise Request Management: An Overview.
– Join the discussion in the Enterprise Request Management group on LinkedIn.

A conversation with Cristian Salanti, Digital Workplace Strategist Here's an uncomfortable truth about...

AI models change every few months. Your enterprise workflows shouldn't have to change with them....

The BPM market is projected to reach $65–70 billion by 2032. Yet roughly 70% of BPM programs never...