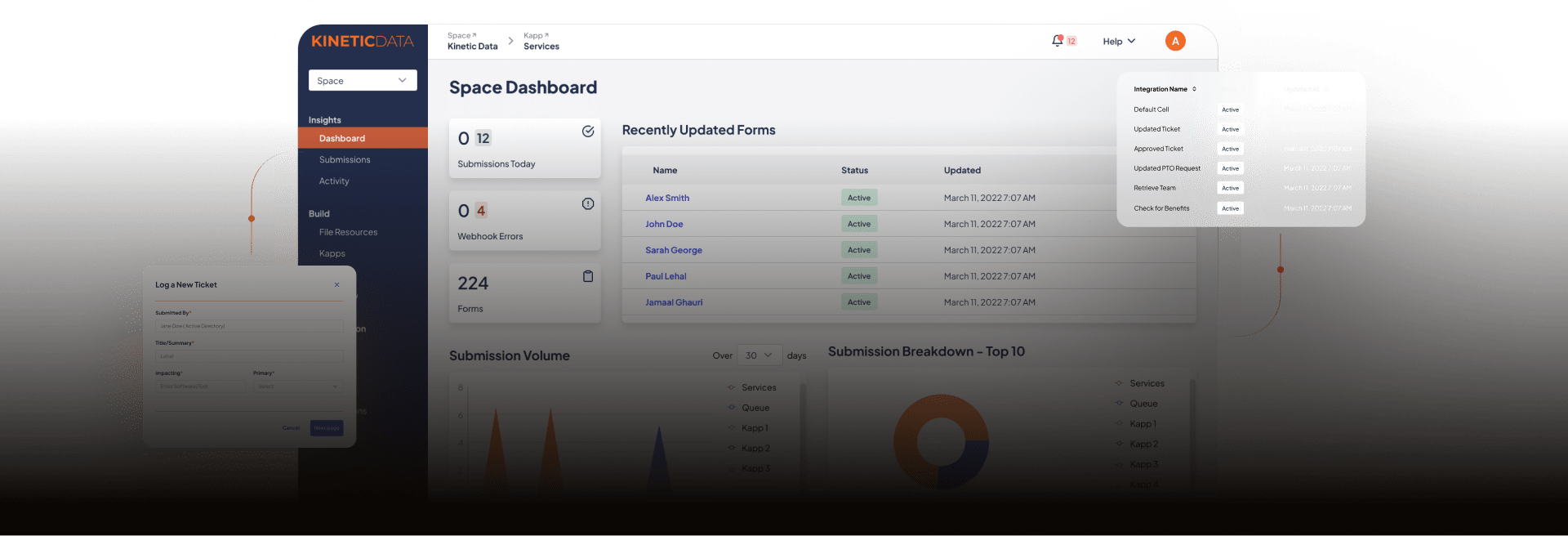
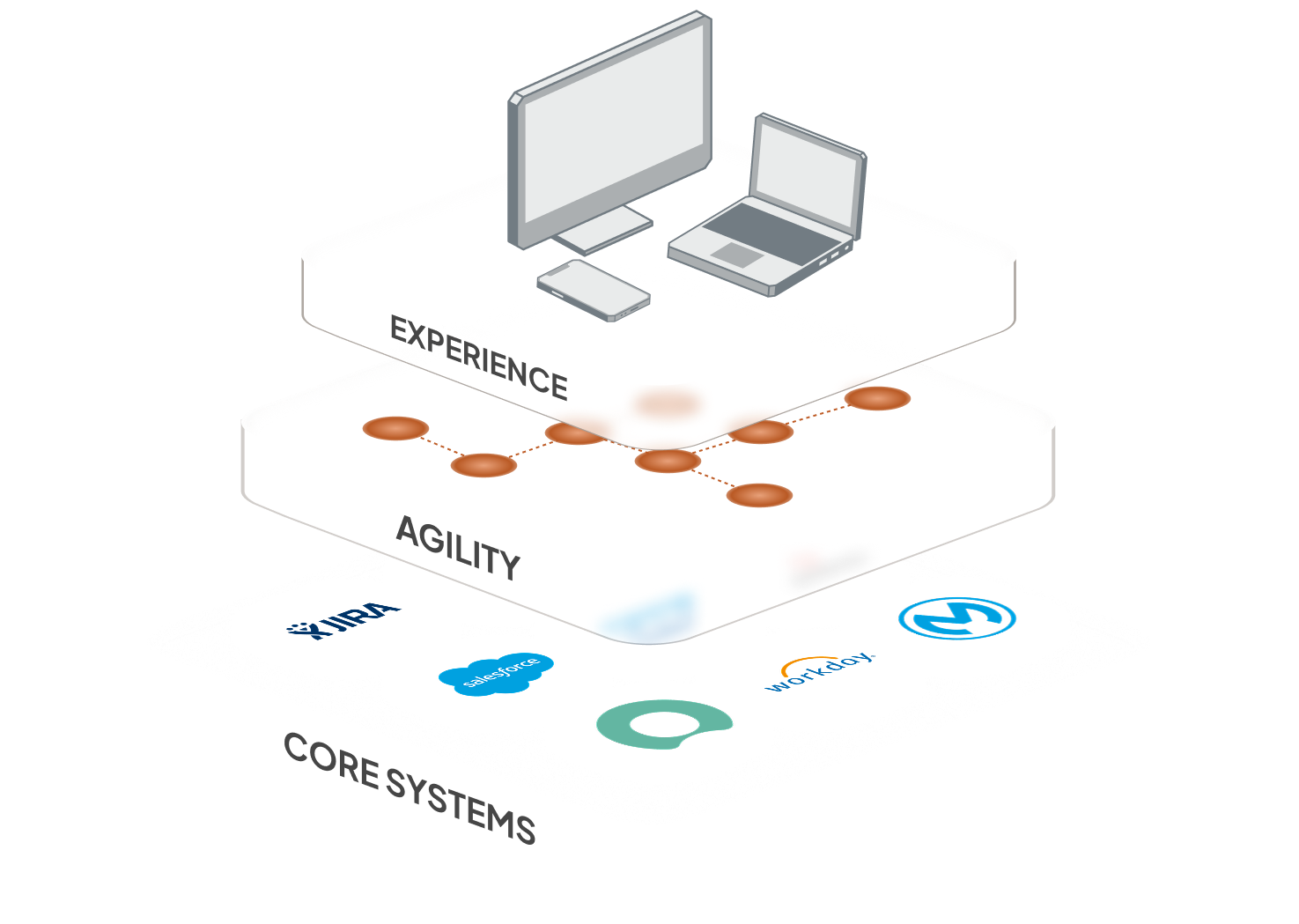
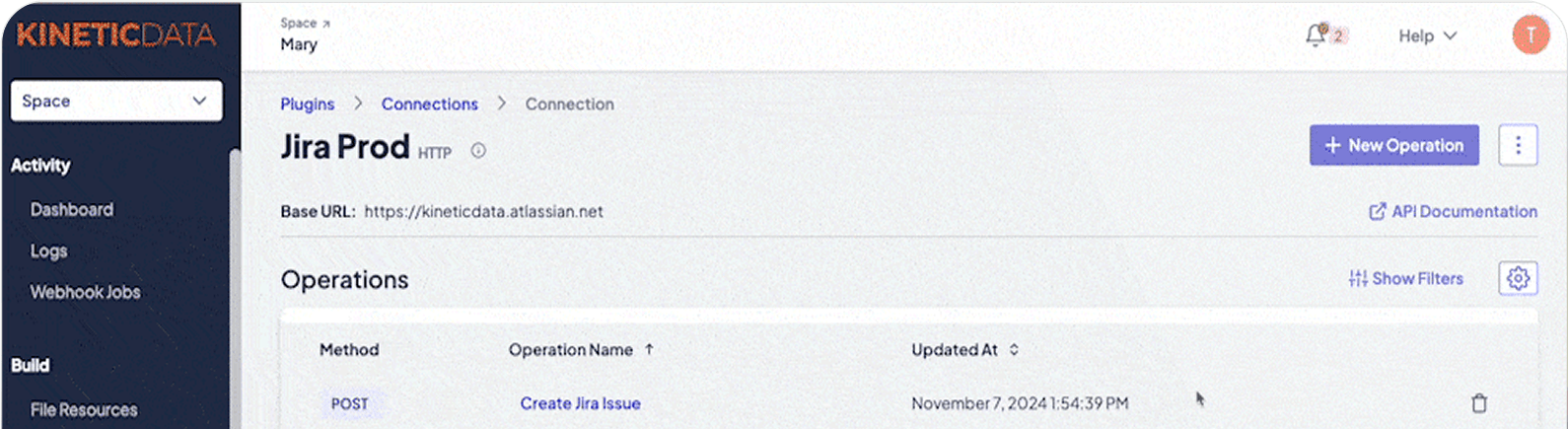
Kinetic provides the controls to secure access, manage operations, and run where you need—cloud, on-prem, or restricted networks—so you can meet your organization’s governance and security requirements.
Kinetic’s Foundation & Governance layer gives enterprises the flexibility and control to operate confidently in complex, regulated, or distributed environments. It combines secure access, flexible deployment, and operational visibility—helping teams align the platform to their existing compliance standards and policies.