Composable AI Architecture: How to Build Modular AI Systems That You Actually Control
AI models change every few months. Your enterprise workflows shouldn't have to change with them....
As 2015 winds down, IT leaders and their teams are looking at internal needs and external conditions in formulating plans and setting budget priorities for the coming year.
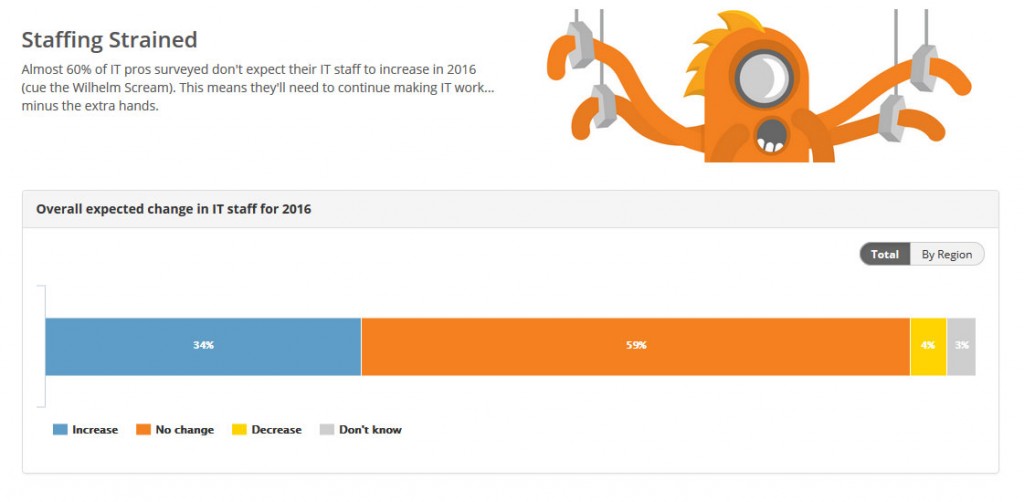
As 2015 winds down, IT leaders and their teams are looking at internal needs and external conditions in formulating plans and setting budget priorities for the coming year.
The recently released 2016 State of IT Report from Spiceworks provides a wealth of information about how IT teams are formulating plans for the year ahead.
The report covers IT budgets, spending and staffing plans; the trends and concerns keeping IT pros up at night; and a look forward at technology adoption trends.
Among the abundance of facts and stats presented, here are three noteworthy findings, along with additional observations.
One of the key top-level conclusions reported by Spiceworks is: “IT pros don’t expect their IT staff to increase in 2016, which means they’ll need to keep doing more… with less.”
At the same time, more than half of IT organizations say “end-user need” is a key purchase driver.
How can IT groups simultaneously improve their own efficiency and better serve user needs?
One highly effective answer is to adopt an enterprise request management (ERM) approach for employee it provisioning and service management. The ERM strategy combines a centralized, intuitive request portal (a.k.a., an enterprise service catalog) with back-end approval and fulfillment workflow process automation.
Implementing ERM helps IT groups “do more with less” by:
And this approach meets user needs by giving employees one easy-to-use portal for requesting any resources, goods or services needed to do their jobs, while ensuring first-time fulfillment.
Shadow IT, BYOD, and cloud computing combined with the increasing number of news stories about corporate data breaches make information security a top concern for IT pros. Per the Spiceworks report:
“About three-quarters of surveyed IT pros consider their organizations at risk for technology, IT security, and man-made disasters or incidents…Plus, many organizations aren’t conducting regular security audits or updating security practices to help protect against worldwide increase in security breaches. In other words, there’s still a lot of room for improvement when it comes to securing IT environments from the threats lurking in the shadows, especially as news of hacks haunt the headlines.”
Protecting vital corporate data requires a proactive approach to security, combining software (anti-virus, firewall, identity/access management, encryption, etc.), training, and policies with process automation to enforce standards.
It also requires having a response plan and enterprise collaboration software in place enabling information security pros to react quickly if a breach does occur, minimizing the damage or loss while quickly and securely restoring mission-critical operational systems and networks.
The top three tech trends for 2016–in terms of technology enterprises currently use or plan to use next year–are:
The 2016 State of IT Report indicates that IT groups will have to do more (particularly in areas like mobile technology and information security) with relatively flat headcount and budgets in the coming year. These issues along with continued rapid technological change will keep life challenging for IT leads and their teams.
Enterprise request management (ERM) is a business efficiency strategy that can make these challenges a bit less daunting. ERM helps IT teams improve the efficiency of their service operations while simultaneously being more responsive to the needs of users. And the process automation in ERM can also help IT pros better address information security issues, one of their top concerns.

AI models change every few months. Your enterprise workflows shouldn't have to change with them....

The BPM market is projected to reach $65–70 billion by 2032. Yet roughly 70% of BPM programs never...
Automation solutions are transforming the way businesses operate, enabling them to streamline processes,...